In two of previous blog posts, I show you How to Enable BitLocker Recovery Information to Active Directory and How to backup the keys to AD. But it dawned on me that I didn’t answer the question How can you query AD for BitLocker Details? It was obvious to me that you could be done but how you do it? In the blog I will show you what you need to do to query AD for BitLocker details.
First this article assume that you have administrator rights to access the BitLocker Recover Password details. Those steps are NO covered within this blog.
How to Query AD for BitLocker Details via ADUC
As I said, I know that BitLocker keys would be stored in the computer object within AD. But where? Using the MEMDP2 as my example that I used in my previous articles. I open Active Directory Users and Computers (ADUC).
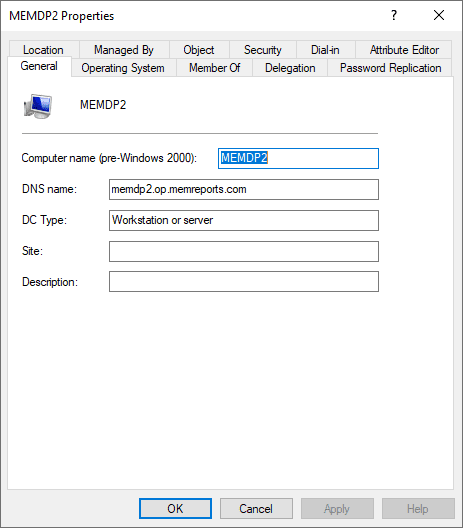
I located memdp2 and looked at its properties, at first glance, there is nothing to indicated that this computer has a BitLocker Password. And no Password Replication will not store BitLocker details but Attribute Editor might. Lets’ start there.
I know from my other research that the are several Attribute that the data is stored within and they are called:
- ms-FVE-KeyPackage
- ms-FVE-RecoveryGuid
- ms-FVE-RecoveryInformation
- ms-FVE-RecoveryPassword
- ms-FVE-VolumeGuid
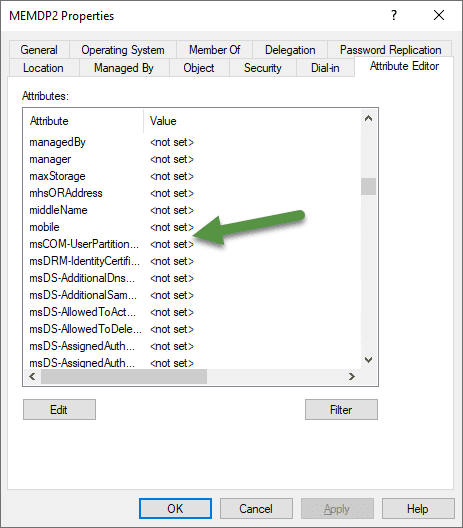
But looking at the Attribute Editor tab, they should be right here! But they are not there, so where are they?
While searching around I found out that you need to install the BitLocker AD module. Since we have all installed a Windows Feature, I’m not going to do a step-by-step guide. Just the high lever steps.
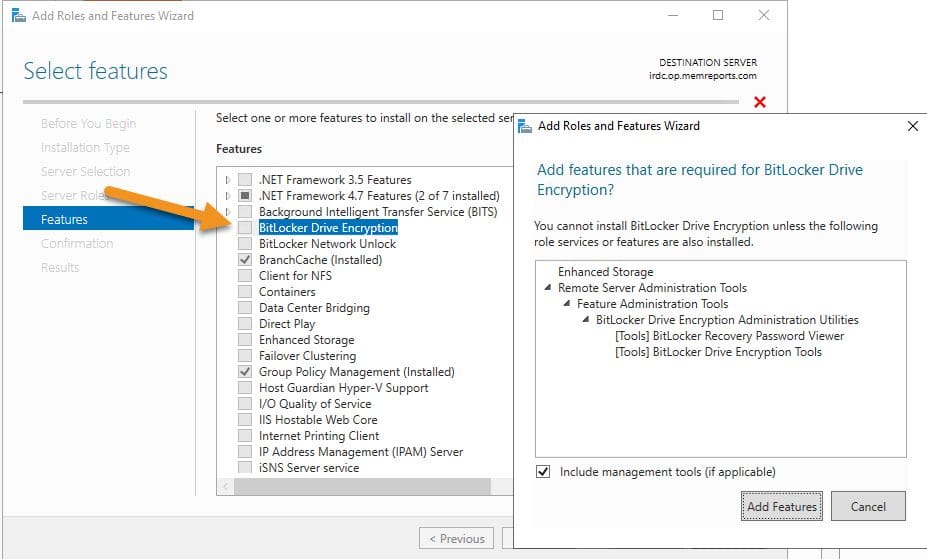
I’m preforming these steps on my DC. In the Features windows, select BitLocker Drive Encryption (orange arrow) this will immediately popup Add more feature window, Click Add Feature button. Complete the wizard to finish the install, don’t forget to reboot.
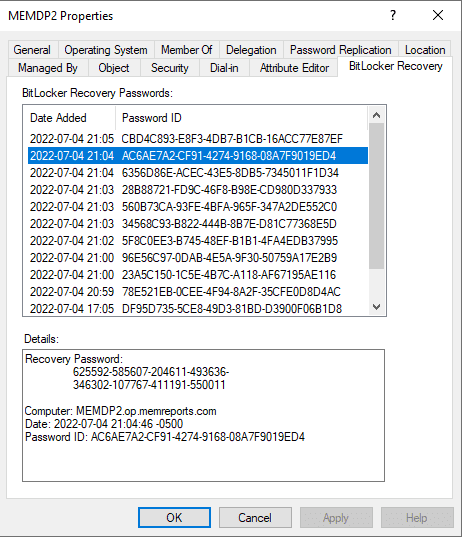
After the reboot I go back into ADUC and select the MEMDP2, we can see the BitLocker Recovery tab. After select it, we see ALL of recovery keys for this server! Can you tell I did a lot of testing on it for my previous articles? This is how to query AD for BitLocker details using ADUC.
How to Query AD for BitLocker Details via PowerShell
It great that you know how to read the BitLocker Password from ADUC but how do you do the same thing via PowerShell?
Before you run the PowerShell command below make sure that you import the AD module. You do that by executing Import-module ActiveDirectory, you will only need to do this once on a computer.
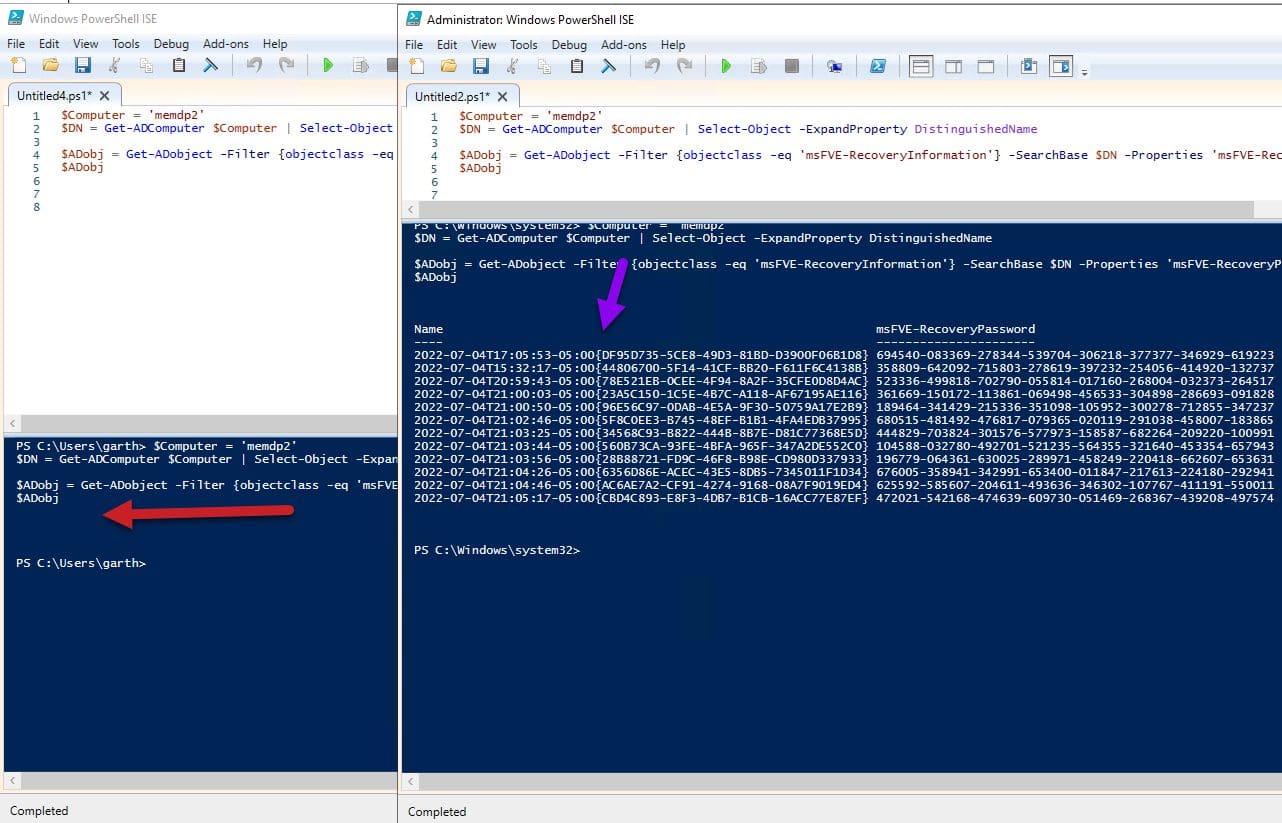
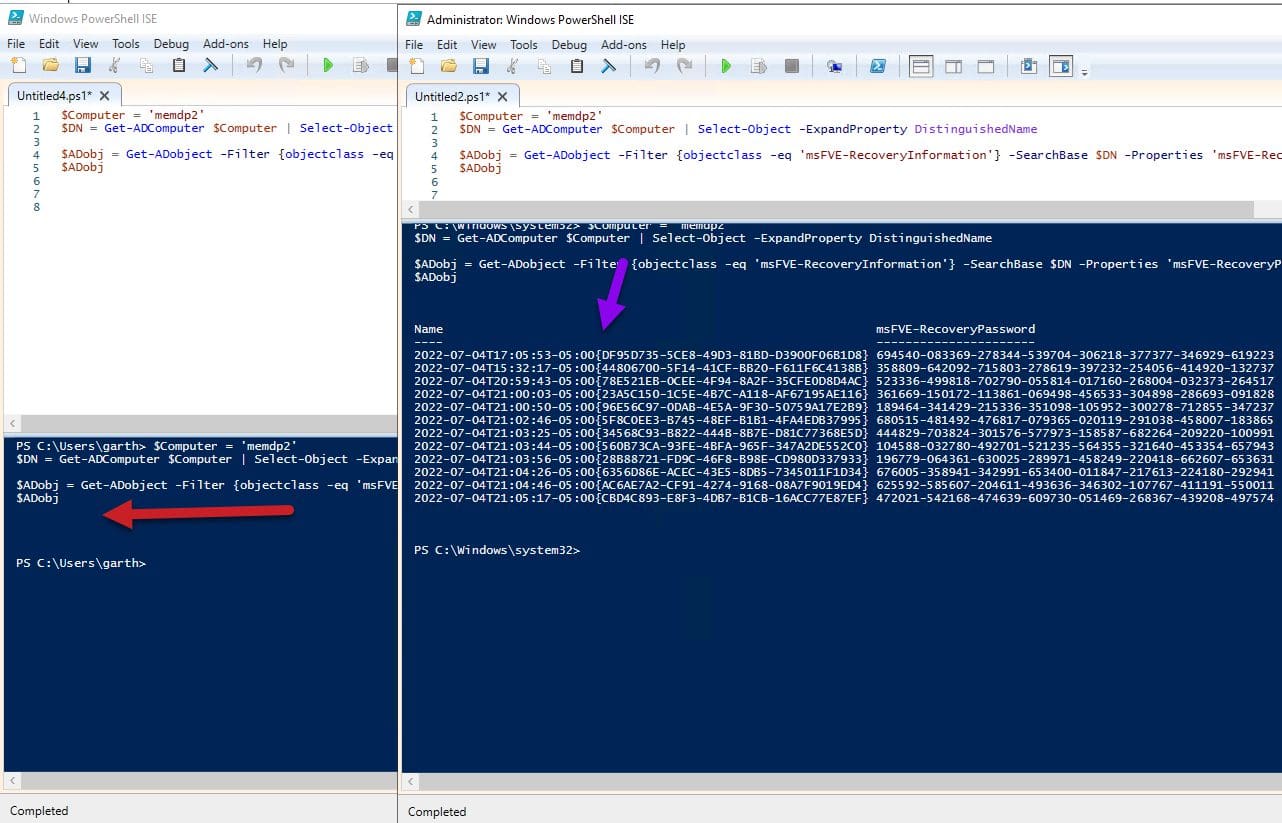
$Computer = ‘memdp2’
$DN = Get-ADComputer $Computer | Select-Object -ExpandProperty DistinguishedName
$ADobj = Get-ADobject -Filter {objectclass -eq ‘msFVE-RecoveryInformation’} -SearchBase $DN -Properties ‘msFVE-RecoveryPassword’ | Select-Object Name,msFVE-RecoveryPassword
$ADobj
The above PowerShell command will query AD for the Recovery Passwords that a computer has.

Again, you can see all of the recover passwords for my same computer.
Tip
If you are NOT seeing any passwords when you run the PowerShell command, make sure that you have run PowerShell elevated.
Now you know how to query BitLocker detail using both PowerShell and ADUC. You next this is to delegate this to your service desk, so that you don’t always have to grab the password for them. If you have any questions, please feel free to touch base @Garthmj.
