While working on another blog on troubleshooting BitLocker, How to Manually Backup BitLocker Recovery Key to AD (coming out next week). I found out that I have not enabled these steps within my own LAB AD. For completeness, I thought that I would document how to store and enable BitLocker recovery information to Active Directory (AD) as a step-by-step guide.
How to Enable BitLocker Recovery Information to Active Directory
Since I covered the details steps on how to create and link as GPO within my article How to Create a Computer Start Up GPO. I will only cover the high-level steps here.
Start by launching Group Policy Management (GPM) DC. Select Create a GPO in this domain, and Link it here… or edit an existing GPO. Give the GPO a name and start editing the GPO.
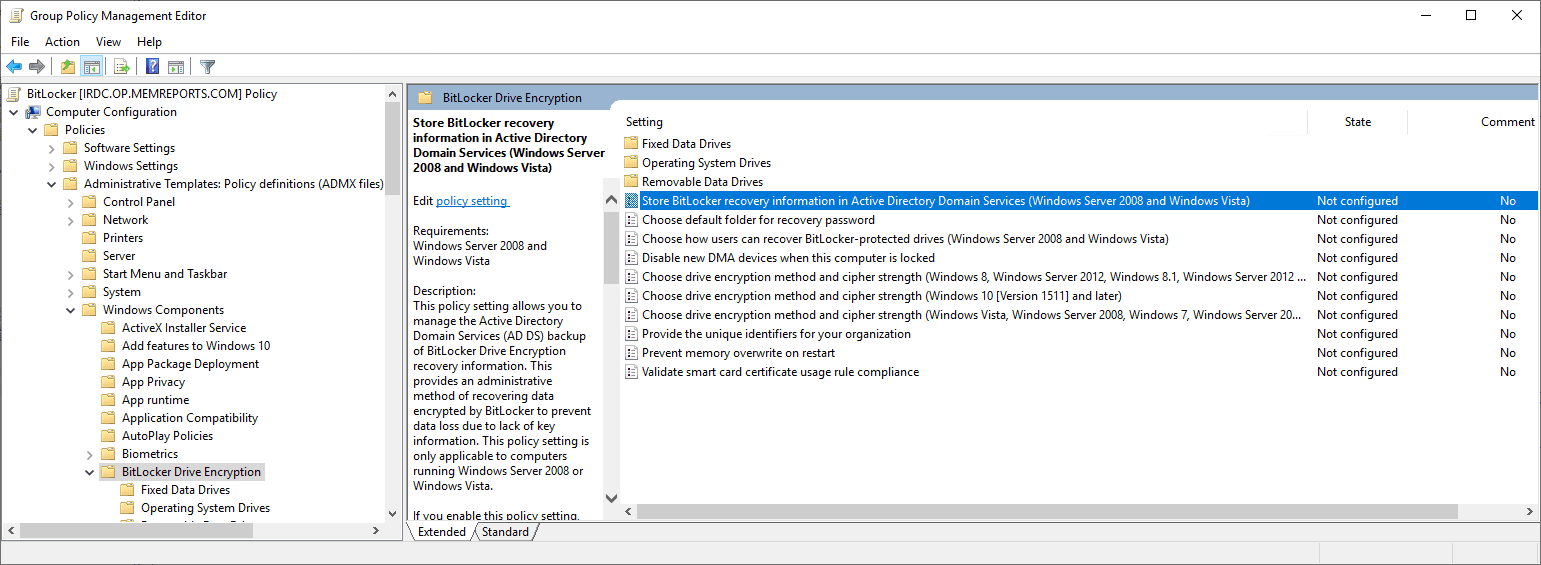
In Group Policy Management Editor (GPME), browse to Computer Configuration | Policies | Administrative Templates: Policy definitions (ADMX files) | Windows Components |BitLocker Drive encryption then double click Store BitLocker recovery information in Active Directory Domain Services (Windows 2008 and Windows Vista).
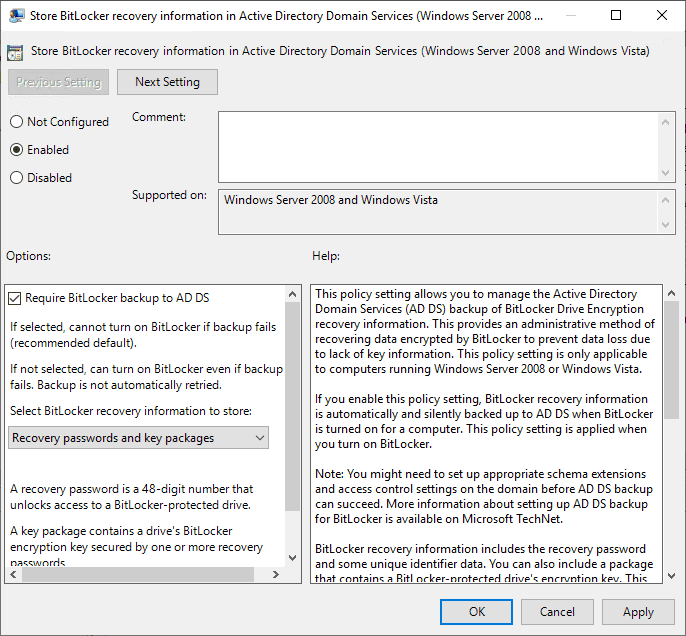
In the popup window, select Enabled before clicking OK.
Chose drive encryption method and cipher strength (Windows 10 [Version 1511] and later)
It is an optional step to configure the encryption method and cipher strength. But I thought that I set the cipher strength to 256 for OS and fixed drives.
There are two drive encryption method (XTS-AES & AES-CBC) and two cipher strength (128 and 256) for a total of four different options. Learn more about the different drive encryption methods or cipher strengths via a Bing / Reddit search will help. Or check out Wikipedia Disk encryption theory. In simple terms, XTS-AES is the latest and greatest, and 265 bit is better than 128 bit.
I changed the defaults to XTS-AES 265-bit OS drives and fixed drives. But I will left USB as the default of AES-CBC 128-bit.
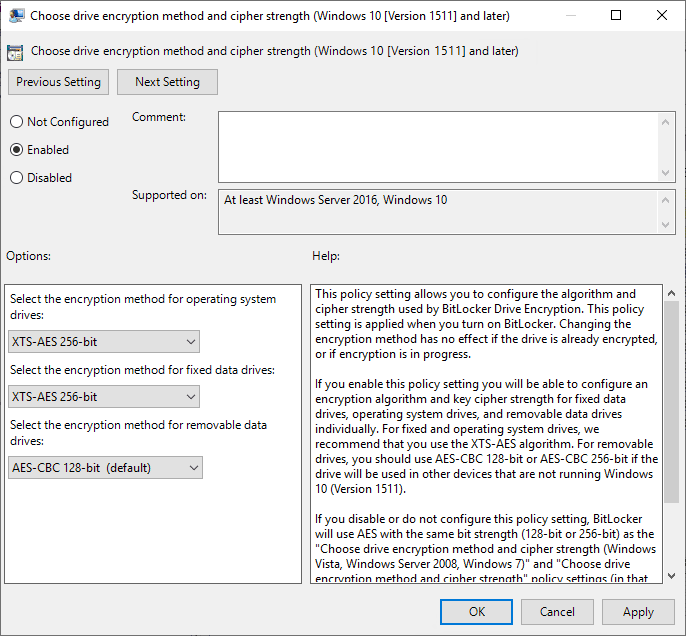
In GPME, double click Chose drive encryption method and cipher strength (Windows 10 [Version 1511] and later). Select Enabled, Select the drop down below Select the encryption method for operating system drives: and select XTS-AES 265-bit, then repeat for Select the encryption method for fixed data drives: and select XTS-AES 265-bit. Click OK to complete.
OS drive options
Enabling the next two GPOs will stop the BitLocker wizard from prompting to save the recover keys on a USB, another drive or printed.
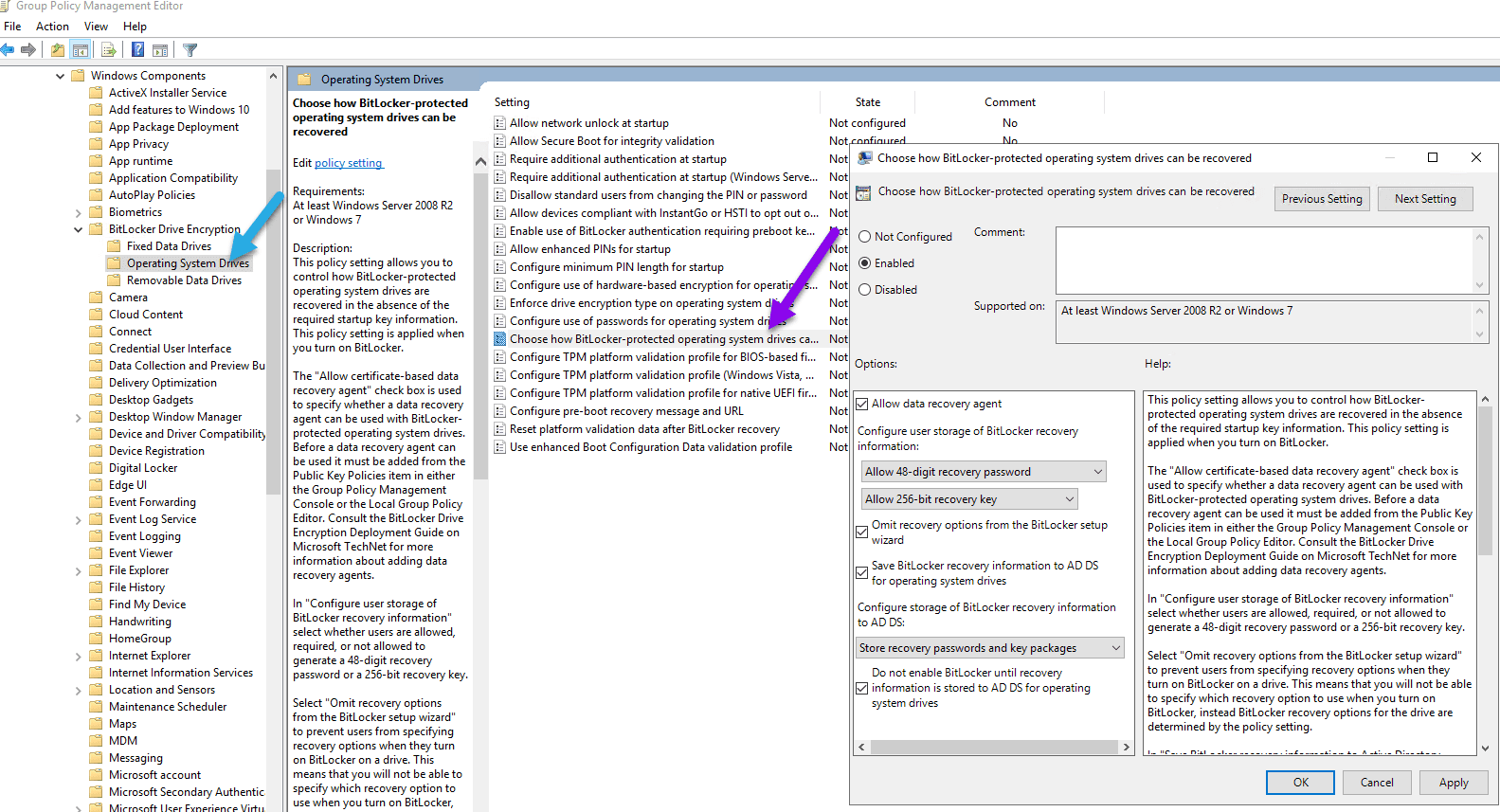
In GPME, expand Operating System Drives folder. Double-click Chose how BitLocker-Protection operating system drives can be recovered. Select Enabled button. Select Enable for both Omit recovery options from BitLocker setup wizard and Do not enable BitLocker until recovery information is stored within AD DS for operating system drives. The click OK to close the window.
Fixed drives options
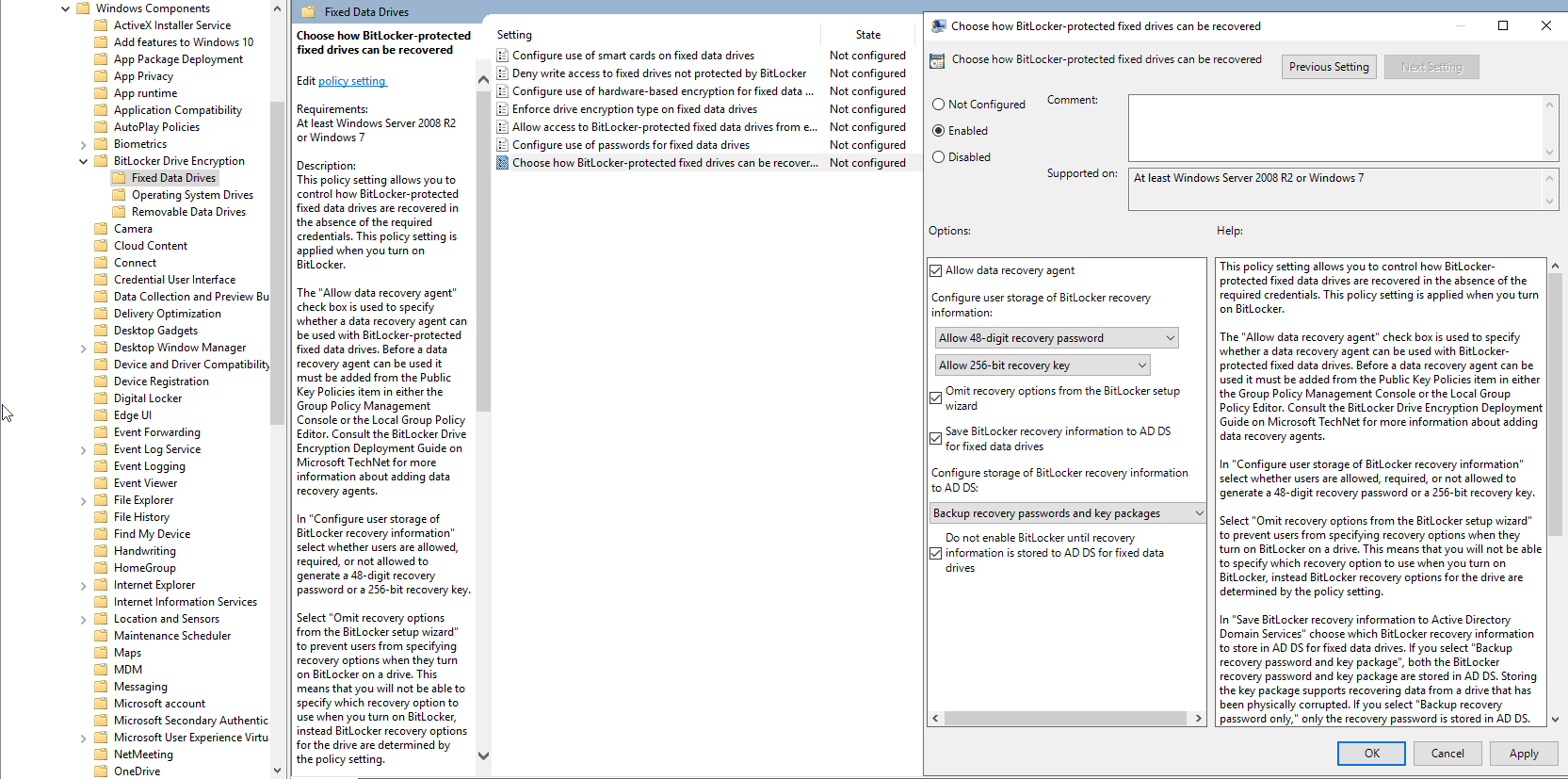
In GPME, expand Fixed Disk Drives folder. Double click Chose how BitLocker-Protection operating system drives can be recovered. Select Enabled button. Enable Omit recovery options from BitLocker setup wizard. Enable Do not enable BitLocker until recovery information is stored within AD DS for operating system drives. The click OK. Close GPME.
Computers will have BitLocker using XTS-AES 265-bit encryption and cipher strength and keys in AD. If you have any questions, please feel free to touch base @Garthmj.
