Last updated on August 13th, 2022 at 09:55 am
Recently, I was helping someone troubleshoot and issue with BitLocker and is storing its key within AD. In other words, to help troubleshoot this issue, we needed to ensure that we could manually backup BitLocker recovery key to AD. They asked how do you do that? Therefore, I created a troubleshooting document , which I emailed to them. As a result, I turn this into a blog post on How to Backup BitLocker Recovery Key to AD.
Most importantly, it is important to remove as many variables as possible. I started with showing you how to backup BitLocker recovery key to AD from the command prompt. After that, we will do the same task via PowerShell.
Backup BitLocker Recovery Key to AD
Firstly, start by opening an elevate command prompt.
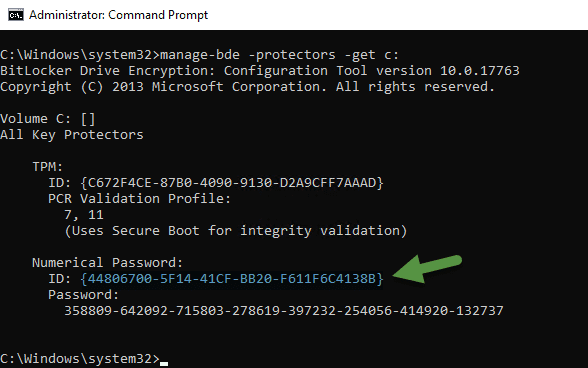
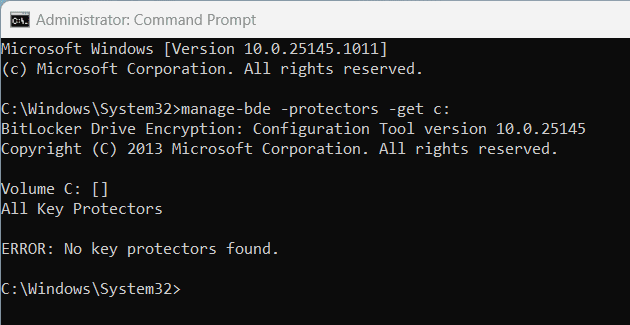
Secondly, Enter manage-bde -protectors -get c:
Make note of the Numerical Password ID in my case: {44806700-5F14-41CF-BB20-F611F6C4138B} (highlighted in blue with the green arrow)
Next in step two.
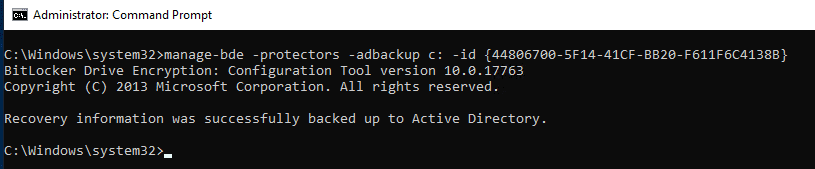
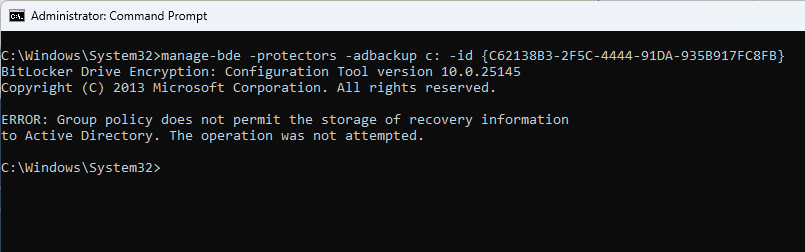
After that, within the CMD type manage-bde -protectors -adbackup c: -id {44806700-5F14-41CF-BB20-F611F6C4138B}
Nextly, Replace ID recorded in steps 1.
Using Power Shell to Backup BitLocker Recovery Key to AD
After that, using PowerShell script below you can do both steps within one script. This is how you backup your BitLocker password to AD.
$BLV = Get-BitLockerVolume -MountPoint "C:"
$KeyProt = $BLV.KeyProtector | Where-object{$_.KeyProtectorType -eq "RecoveryPassword"}
$KeyProt.KeyProtectorId
Backup-BitLockerKeyProtector -MountPoint "C:" -KeyProtectorId $KeyProt.KeyProtectorId
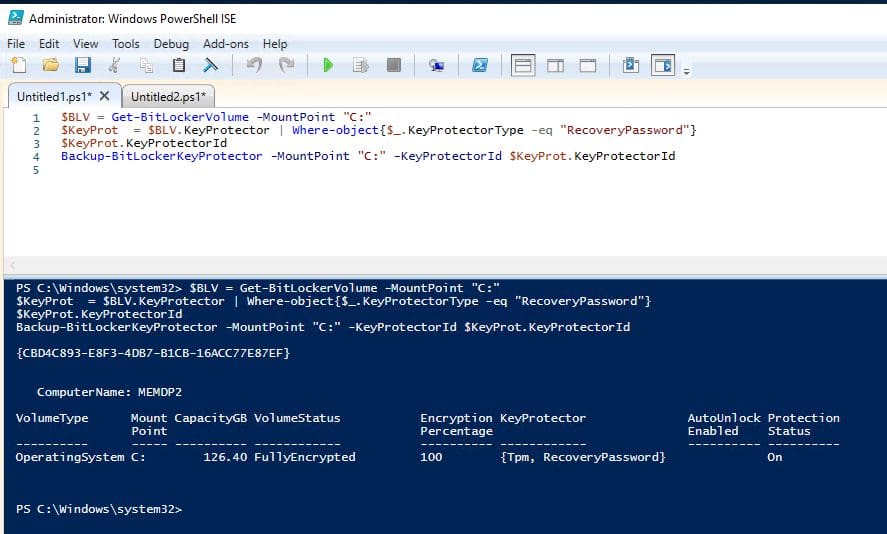
You can see that the key protector id and that there was no error backing up to AD.
How to Rotate the BitLocker Recovery Password
Therefore, once you give the BitLocker password out to anyone, you will want to change it. The easiest way to do this is via PowerShell.
$BLV = Get-BitLockerVolume -MountPoint "C:"
$KeyProt = $BLV.KeyProtector | Where-object{$_.KeyProtectorType -eq "RecoveryPassword"}
$KeyProt.KeyProtectorId
Remove-BitlockerKeyProtector -MountPoint "C:" -KeyProtectorId $KeyProt.KeyProtectorId
Add-BitLockerKeyProtector -MountPoint "C:" -RecoveryPasswordProtector
$BLV = Get-BitLockerVolume -MountPoint "C:"
$KeyProt = $BLV.KeyProtector | Where-object{$_.KeyProtectorType -eq "RecoveryPassword"}
$KeyProt.KeyProtectorId
Backup-BitLockerKeyProtector -MountPoint "C:" -KeyProtectorId $KeyProt.KeyProtectorId
Resume-BitLocker -MountPoint "C:"
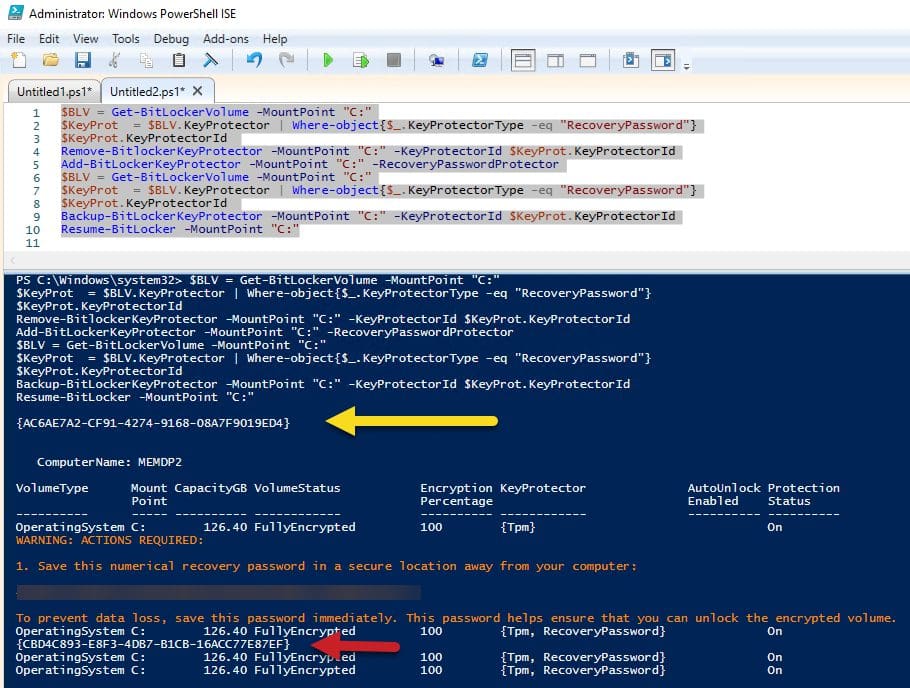
You can see from screenshot, for instance, that the key protector id changed verse when it first queried it.
ERROR: Group policy does not permit the storage of recovery information to Active Directory. The operation was not attempted.
To store BitLocker keys, configure AD. For more details see How to Enable BitLocker Recovery Information to Active Directory.
ERROR: Group policy does not permit the storage of recovery information to Active Directory. The operation was not attempted.
ERROR: No key protectors found.
The computer does not have BitLocker Enabled. Turn on BitLocker and try again.
What else would you like to know about BitLocker and MECM? If you have any questions, please feel free to touch base @Garthmj.
